Network Situational Awareness
Network situational awareness is an area where Empire shines. By taking advantage of the functionality of PowerView, Empire implements a variety of functions to assist with gathering network information.
The situational_awareness/network/arpscan module, from DarkOperator’s Posh-SecMod, allows you to perform an ARP scan against a given range of IPv4 addresses. The situational_awareness/network/reverse_dns module (also from Posh-SecMod) lets you reverse-grind IP ranges to determine their DNS hostnames. Also, the situational_awareness/network/portscan module, from PowerSploit, will perform Nmap-style port scanning on a network.
PowerView Functionality
The situational_awareness/network/netview module will execute the PowerView port of @mubix’s netview.exe project. This allows you to flexibly query for hosts from a given domain and enumerate shares, loggedon users, and sessions from each.
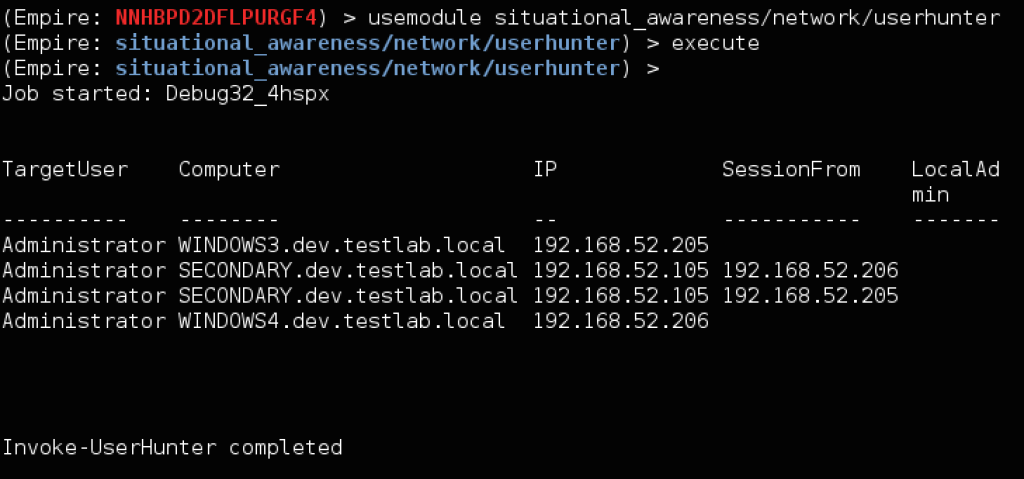
The situational_awareness/network/userhunter and situational_awareness/network/stealth_userhunter modules take this functionality one step further, and give you the ability to hunt for where target user sets are logged in on the network. Userhunter will enumerate every machine it finds, which will give you complete (but noisy) coverage. Stealthuserhunter will take a more subtle approach, by enumerating all likely file servers/domain controllers on the network and enumerating just the sessions against each. This gives you reasonable coverage and is both quieter and faster. For more information on user hunting, see the “I Hunt Sys Admins” post and accompanying presentation.
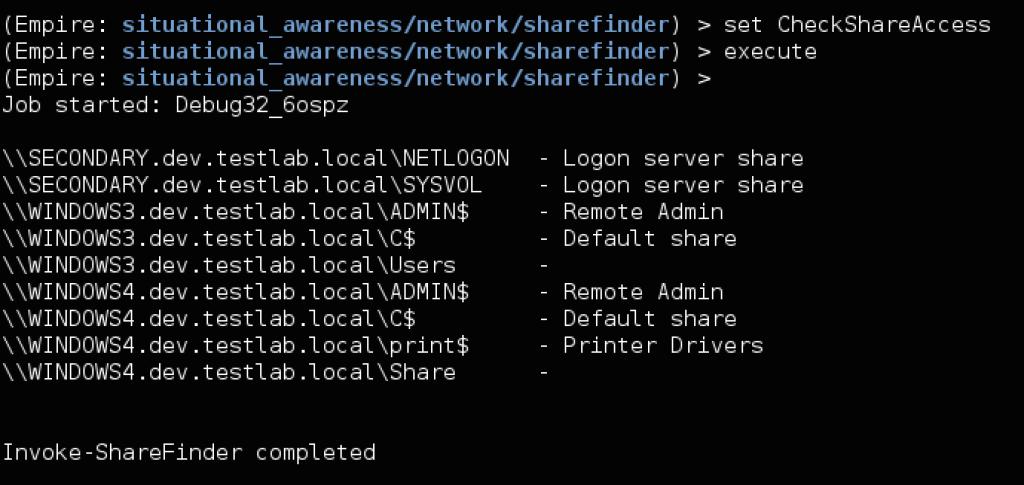
The situational_awareness/network/sharefinder extends the sharefinding capability of netview. It will enumerate all machines on a given domain, and return the available shares for each. Setting the CheckShareAccess option will return only shares that are readable from the current user context. Almost every organization has improperly secured file shares, making this a great place to start data mining for elevation:
The get_computer, get_domaincontroller, and get_user modules will enumerate computer objects, domain controllers, and users respectively. The get_exploitable_systems module attempts to query for systems in the domain likely vulnerable to common exploits. The get_localgroup module is out of our favorites- it will return the members of the local administrators group on a remote host, which can be extremely useful in facilitating later lateral spread.
The map_domaintrusts module will recursively enumerate all reachable domain trusts from your current network position. If you’re interested in domain trust exploitation, you can read more here.